限定的な攻撃に利用される Java のゼロデイ脆弱性
How can you reset apple OS X Password without disk
Source : http://bookingtohosting.blogspot.com/2015/07/reset-apple-mac-os-x-root-or-admin.html
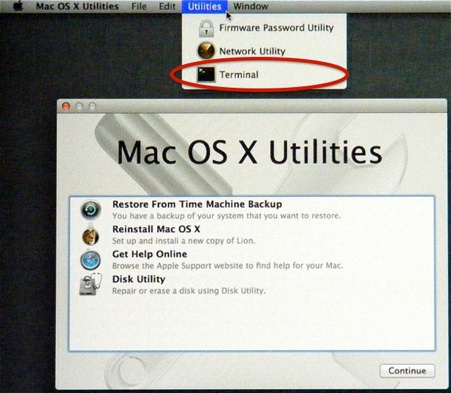
1. Boot into Recovery Partition to Reset Apple OSX Root/Admin Password
Reboot into the Recovery Drive by choosing the ‘Apple‘ menu > Restart, hold down the ‘command’ + ‘r’ keys on the keyboard during the start up process when you see the start up screen (Gray Screen with Apple Logo) you can let go. When the machine boots eventually you will see the OS X Utilities screen.
 |
| Recovery Mode-Reset Apple Mac OS X Root or admin password |
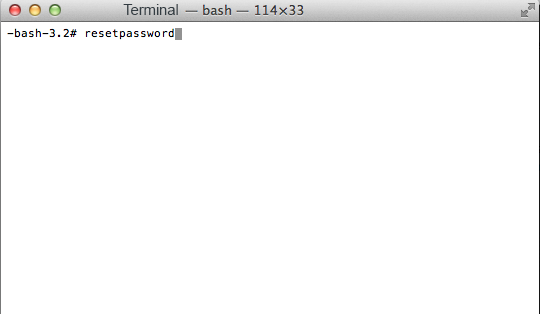
Go to the Utilites menu and select Terminal.
 |
| Reset Apple Mac OS X Root or admin password |
At the prompt type ‘resetpassword’ and hit Enter/Return Key.
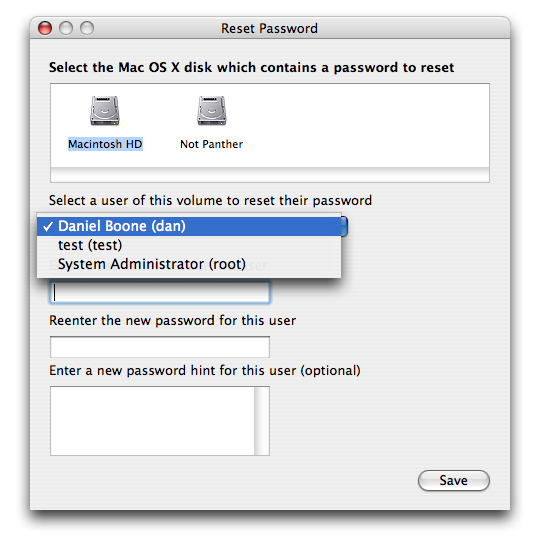
This launches a new Reset Password screen, Where you can select the Volume Hard Drive, containing the user account.select the Volume Hard Drive in the top part of the window pane, then select the user account from drop down list and then Type the New password for this account and confirm the password by typing again, and click save, you get a confirmation screen and details about the keychain account.
 |
| Reset Apple Mac OS X Root or admin password |
 |
| Reset Apple Mac OS X Root or admin password |
Note: Do not click on the Reset button at the bottom because that is used to reset permission and access control list of all the files and folder in selected user's home directory.If you by mistake click on that its gonna take a long time to repair the permissions.
2. Use Your Apple ID to Reset Password
Starting with 10.7 Lion, it also became possible to use your Apple ID to reset your administrator password. It’s turned on by default in the Users & Groups pane of System Preferences, but double-check to make sure.
 |
| Reset Apple Mac OS X Root or admin password |
When this feature is active, if you enter the administrator password incorrectly at the login window three times, a popover appears with the password hint and a message saying “If you forgot your password, you can reset it using your Apple ID.” Here’s how to do that:
 |
| Reset Apple Mac OS X Root or admin password |
 |
| Reset Apple Mac OS X Root or admin password |
- Click the arrow icon to open the Reset Password dialog.
- Enter your Apple ID and its password, then click Reset Password to proceed.
- Enter a new administrator password, verify it, and fill in the Hint field so that you’ll get a memory trigger the next time you forget.
- Click Reset Password, and you’re done.
B. Reset Admin/Standard user password in OS X 10.6, 10.5 and 10.4
Mac OS X 10.6 and earlier did not come with Recovery partition so you will need to use the installation Disk to boot Mac from installation Media and then get to the terminal just like in recovery mode to reset password.But there are other simple methods to reset password that does not require an Installation Disk.
This only works for Apple OS X 10.6 Snow Leopard.
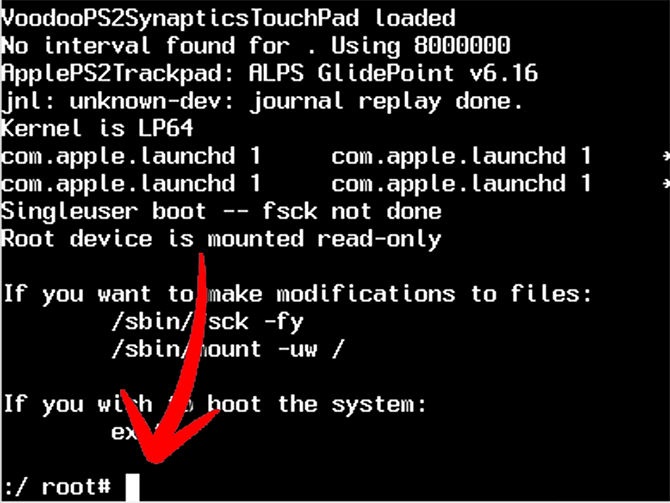
1: Reboot the computer and hold the command and S keys down to enter single user mode.
You will need a wired/built in keyboard, a PC one will work, the Windows key is the commnad key.
(if a lock appears and a password request, there is a firmware password, you have to know it or take it to Apple to fix it)
 |
| Reset Apple Mac OS X Root or admin password |
2: When you get control, type fsck -fy and press enter, it will take a bit to finish
3: Next type mount -uw / (there is a space before and after -uw) this mounts the drive
 |
| Reset Apple Mac OS X Root or admin password |
4: Next type ls /Users this will list the Users on the machine so you can get the name of the user whom you want to reset the password for.
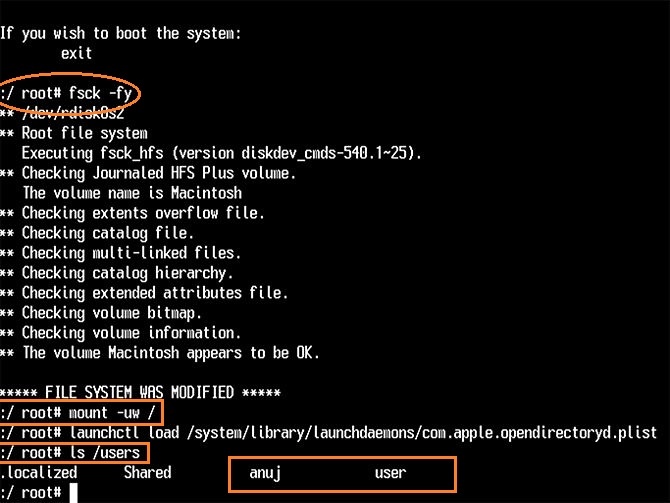 |
| Reset Apple Mac OS X Root or admin password |
5: Next type passwd username (where username is the name of the account for example to reset password of user "anuj" type passwd anuj)
6: Enter the new password twice, you won't see anything.
7: Then type command "Exit" or "Reboot" and hit enter to restart the Mac.
8. After you restart and login you will be getting a message related to Keychain so you could create a new key chain here.
To read this complete article you can refer to this post http://bookingtohosting.blogspot.com/2015/07/reset-apple-mac-os-x-root-or-admin.html
U.S. Commerce Department Controversial Cybersecurity Rule Will Weaken Security Industry and Worldwide Protections
In May 2015, the United States Department of Commerce published a proposed amendment to the U.S. export regulations that would cover cybersecurity products. While the proposed rule may have been well-intentioned to protect national security interests and preserve human rights, the unintended consequences and practical results of implementation would have far-reaching and detrimental effects on the cybersecurity industry.
The proposed rule would severely damage legitimate vulnerability research and security testing worldwide, and thus undermine our ability to protect our own networks and to innovate cybersecurity products and services. The end result is that our customers – businesses, governments and consumers – would be less secure and at greater risk.
The proposal was precipitated by U.S. commitments under the Wassenaar Arrangement, a 41-country export control agreement that was designed to cover arms and dual use technologies and did not originally envision cybersecurity. Though the Arrangement is not binding, it has been the policy of the U.S. government to fully implement agreements under the Arrangement and to update the export control regime accordingly.
The Commerce Department should reconsider this proposed rule, as the cybersecurity industry and those we serve will be impacted in the following ways:
Access to legitimate cybersecurity tools would be restricted, as the export of cybersecurity technologies and testing tools would be constrained, even to overseas subsidiaries of U.S. companies.
Research into cybersecurity vulnerabilities would be curtailed, as researchers would be hindered from testing networks and sharing technical information across borders.
Collaboration on cybersecurity risks would be harmed both within cybersecurity companies and with customers and industry partners, as information would be deemed “exported” if it is shared with non-U.S. persons, even if they are physically located in the U.S.
While the rule is directed at companies that create or sell “intrusion software” used to breach systems, its broad language will affect a wide array of legitimate cybersecurity research and network penetration testing. As a global security company, with researchers based around the world, this regulation could require our American researchers to obtain a government license in order to have more than a cursory conversation about new security vulnerabilities with their co-workers overseas. It also appears likely that we would need a new license every time we conduct defensive network testing for one of our own business units or a customer that resides outside the U.S.
In Symantec’s 2015 Internet Security Threat Report, we highlighted that cyber attackers are becoming more and more sophisticated and leapfrogging defenses of organizations of all sizes. In fact, nearly one million new malware variants are created every day, and there was a 40 percent increase year-over-year in targeted attacks against large enterprises. The current threat landscape requires real-time security analysis, testing and deployment of protections. Asking a multinational corporation who is at risk of a cyber attack to wait months for a license to be able to test its network defenses, or to receive the latest protections because its security provider is hampered from communicating across borders, is downright dangerous.
In addition, information sharing – a longstanding U.S. policy priority – would also be inhibited. The rule would have a chilling effect on the security community writ large as sharing details about vulnerabilities and exploits with experts outside the U.S. could be prohibited without first obtaining an export license. The simple fact is that the rule will not do anything to curtail illicit hacking and intrusions. As drafted, the rule would do just the opposite. It will handcuff legitimate security companies and researchers while imposing no restrictions on cyber criminals. Ultimately, this will put citizens, businesses, and governments at greater risk of cyber attacks.
The Commerce Department should reconsider the proposed rule and move for further discussion and analysis of the current agreement at the next Wassenaar Plenary meeting in 2016.
Remove the Uninterrupted Export from VAC
Ok so I've taken over anEV enviroment and there was an issue whereby I was Unable to delete uninterrupted exports.
SOLUTION:
Was unable to delete the Uninterrupted Export from VAC.
Error: Unable to generate the export information. Could not retrieve the information for Vault “Archive Id”. Unspecified error
Ran command in SQL and got the Job Description: "Export Archive Name"
Confirmed backup was completed.
Use EnterpriseVaultDirectory
Select * from AdminJobEntry
Took Backup of SQL Databases and ran command to Delete the Admin Job
Use EnterpriseVaultDirectory
Delete from AdminJobEntry where JobDescription ="Export Archive Name"
Checked and Uninterrupted Export was no longer present.
Hope this helps someone.
Microsoft Patch Tuesday – July 2015

続きを読む
「Forkmeiamfamous」: Duke グループ最新の攻撃、Seaduke が登場
Industrial Internet 4.0
This quick post simply seeks to set context for software leaders hoping to help with the Industrial Internet, or “Industry 4.0” as many say in Europe, just highlighting a few points commonly missed by software leaders first stepping into industrial settings, particularly with the recent multi-hundred billion dollar projections on the size of the market for industrial internet software.
Unfortunately, many of us with strong backgrounds in software don’t often realize the scale of time and cost at which most industrial plants operate. Relining a blast furnace can cost $100M. In auto manufacturing, each minute of downtime for a manufacturing plant costs $22,000 on average. That’s $1.3M per hour, nearly three times more expensive than unplanned downtime costs for the average Information Technology (IT) organization. Some pipelines move $32,000 of oil per minute. That’s over $1.9M per hour. In that context, it’s no wonder that plant operations teams often view planned and unplanned maintenance with a bit more intensity than most IT teams. It’s also no wonder that companies are investing aggressively to optimize systems where a 10% improvement can produce gains of more than $200M per year for typical manufacturing plants. It's equally clear why "security" means "availability" to these operational teams who have so much need to protect the uptime and integrity of these systems. That's in direct contrast to traditional Information Technology (IT) teams who often must protect "confidentiality" and "secrecy" at the cost of uptime. That's an important distinction as manufacturing companies look to carefully leverage these smart technologies to improve their performance.
According to many, the past 350 years of manufacturing are marked by three revolutionary advances: the steam engine for generating mechanical power, then electrification of manufacturing, and most recently, digitalization of manufacturing through simple Programmable Logic Controllers (PLC). Many industrial leaders in Europe believe that they can produce a “fourth” such leap, “Industry 4.0,” by lashing digital manufacturing systems into highly virtualized, decentralized, and modular, plants leveraging interoperable real-time systems to yield “smart” factories which outperform current manufacturing plants by the same degree to which mechanization, electrification, and digitalization have improved manufacturing in centuries past. Beyond “linear” improvements such as the “10%” mentioned above, such digitally “integrated” plants will have the flexibility and agility to not only keep pace with increasingly nimble competition, but to stay ahead of them.
Of course, that connectivity brings both tremendous promise and risk. Having belabored pipeline explosions and steel blast furnace damage from cyber attacks in past posts, I won’t repeat myself here, especially since Symantec has already given the “Dragonfly” attacks against Western energy companies such great in depth coverage. However, I will promise here that next month’s blog will propose a path “forward” for security of such next generation Industrial Control Systems (ICS), not only leveraging the cornerstones of security for the Internet of Things (IoT), but also describing how they can be applied to the ICS of the Industrial Internet and Industry 4.0. In the interim, if you’re impatient, feel free to read up on our latest security solutions for embedded systems at www.symantec.com/iot.
For more reading:
http://news.thomasnet.com/companystory/downtime-costs-auto-industry-22k-minute-survey-481017
http://articles.latimes.com/2010/aug/10/nation/la-na-alaska-oil-20100810
http://www.inc.com/yoav-vilner/store-downtime-the-ecommerce-kiss-of-death.html
http://www.stratus.com/stratus-blog/2014/09/26/how-downtime-impacts-the-bottom-line-2014/
http://blogs.gartner.com/andrew-lerner/2014/07/16/the-cost-of-downtime/
マイクロソフト月例パッチ(Microsoft Patch Tuesday)- 2015 年 7 月
Symantec Intelligence Report: June 2015
Welcome to the June edition of the Symantec Intelligence report. Symantec Intelligence aims to provide the latest analysis of cyber security threats, trends, and insights concerning malware, spam, and other potentially harmful business risks.
There is good news this month on the email-based front of the threat landscape. According to our metrics, the overall spam rate has dropped to 49.7 percent. This is the first time this rate has fallen below 50 percent of email for over a decade. The last time Symantec recorded a similar spam rate was clear back in September of 2003.
Phishing rates and email-based malware were also down this month. However, there were 57.6 million new malware variants created in June, up from 44.5 million pieces of malware created in May and 29.2 million in April. This increase in activity lends more evidence to the idea that, with the continued drops in email-based malicious activity, attackers are simply moving to other areas of the threat landscape.
Ransomware attacks are up in June, with over 477,000 detected during the month. While still below the levels seen at the end of 2014, this is the second month in a row ransomware attacks have increased since they reached a 12-month low in April. Crypto-ransomware is also up in June, reaching the highest levels seen since December 2014.
In other news, after a busy month in May targeted attacks against the Manufacturing industry leveled out in June, dropping from 41 percent to 22 percent. Manufacturing still comes out on top in terms of sectors subject to targeted attacks, but activity is now in line with what is being seen in the Finance, Insurance, & Real Estate sector and the Services – Professional sector, which come in at second and third place.
We hope you enjoy the June Symantec Intelligence Report. You can download your copy here.
Veritas Talks Archiving Office 365
#VtasPart can #Learn_Central with @veritastechco to replay this weeks
#Archiving & #Office365 webinars #ondemand at http://bit.ly/1Jk6Cg5
Log-in to PartnerNet http://bit.ly/1zVNBCA and click the links below to watch this weeks webinar replays:
Veritas Talks Archiving: http://bit.ly/1McF9TP
1: Articulate the value of automated retention and life cycle management.
2: Identify Enterprise Vault opportunities and overcome the key objections.
3: Increase account control and find upsell/cross sell opportunities
Veritas Talks Archiving Office 365: http://bit.ly/1MwglDn
1: Position Enterprise Vault as an Information Governance solution
2: Learn how Veritas can address Office 365 capability gaps
3: Simplify Office 365 migrations and reduce business risk.
We look forward to supporting your learning journey in the Veritas Expert Community http://bit.ly/1HJcyi3
How to migrate/upgrade a SCSP/DCS database/server to a new instance.
Problem
1) SCSP/DCS was setup on machine that is now below needed specifications.
OR
2) You would like to use a new SQL Server instance such as 2012 instead of 2008.
OR
3) You want to migrate from SCSP to DCS without losing the SCSP data base.
Solutions
Things to Consider When Moving the Symantec Critical System Protection (SCSP) Database and Management Server
https://support.symantec.com/en_US/article.TECH116309.html
How to Move the SCSP Database to a new SQL Database Server
https://support.symantec.com/en_US/article.TECH116276.html
How to Move a manager or DB to a new server
How can I ignore IPS events that I do not want to see?
Problem
You know the IPS event is present and know why it is occurring, but do not want to keep being bombarded with the events.
Solution
Create a log Config policy
In order to ignore IPS events you don’t want to see you will need to create a new log rule.
- Go to the Configs tab

- Select Prevention

- Select ADD

- Create an Empty Policy

- Select Edit

- Select Log Rules
![Screen Shot 2015-07-14 at 10.29.08 AM.png]()
- Clear the list hitting the red X
![Screen Shot 2015-07-14 at 10.29.51 AM.png]()
- Click apply then okay
- Select the policy then click apply
![Screen Shot 2015-07-14 at 10.30.39 AM.png]()
- Apply the policy to a client or group
![Screen Shot 2015-07-14 at 10.31.21 AM.png]()
- Events should no longer trigger for that client or group
Specify a proxy server for the reputation lookups in DCS
Problem
Your DCS setup is running behind a proxy and reputation lookups are not being completed.
Solution
The reputation data relies on the shasta data and not LiveUpdate. Lots of users have DCS set to run behind a proxy which prevents direct access to the Internet. At this point in time you cannot specify proxy settings for reputation lookups in DCS. By being setup behind a proxy this aspect of DCS does not function. At this point in time there is no direct solution to your problem.
Unifying the Software Defined Data Center
After 15 years in the industry I have seen a lot of “truths” as hardware, software, and deployments have evolved. While not all of them have panned out, there are two that continue to prove themselves:
- Applications drive the business
- Data is the gas for those applications
 While individually each has spawned new industries and markets, one cannot function without the other. In the consumer world my iPhone and its apps are the best thing in the world…until there’s no data source. Conversely, my full bar connection is meaningless when Safari keeps crashing while loading a website.
While individually each has spawned new industries and markets, one cannot function without the other. In the consumer world my iPhone and its apps are the best thing in the world…until there’s no data source. Conversely, my full bar connection is meaningless when Safari keeps crashing while loading a website.
The same is true in the enterprise. Enterprises have, and will continue to, spend untold billions on trying to stitch together disparate solution and point tools to do one basic thing: Keep the Application and its Data accessible. While not impossible, trying to piece together solutions takes highly trained and skilled workers to build the basic foundation of an application infrastructure. All the effort and training in the world doesn’t guarantee that the next upgrade of any single component of your business service won’t compromise that hard fought stability.

At Veritas, we take a unified, software defined approach to managing storage and application availability through a single integrated solution. Veritas InfoScale is the truth when it comes to providing a software defined data center. Through advanced storage management, unmatched vendor and platform support, and best in class application insight, InfoScale enables the business service to be architected to meet the three legs of the SLA stool: Performance, Availability and Cost. Avoiding the piecemeal of point solutions, InfoScale is a single solution for the enterprise to keep the world running and information flowing as life happens.
Addressing Recent Events Regarding Code Signing Certificates
続きを読む
Expanding Symantec’s Cyber Career Connection (SC3) to India!

Mike Brown, Symantec President & CEO, and R. Chandrashekhar, President, NASSCOM sign a Memorandum of Understanind (MoU) for "Buidling Cybersecurity Skills"
In June of last year, standing alongside Secretary Hillary Clinton at the Clinton Global Initiative America meeting, Symantec first launched the Symantec Cyber Career Connection (SC3). Almost one year to the day, President and Chief Executive Officer of Symantec Michael A. Brown joined R. Chandrashekhar, President of the National Association of Software and Services Companies (NASSCOM), in announcing the expansion of SC3 to India. SC3 is designed to help close the cybersecurity skills gap by attracting, educating, and training underserved young adults for careers in cybersecurity. We’ve followed the U.S. pilot program throughout the year – from meeting the dedicated partners, Year Up and NPower, to hearing from the students and their journey in the program – and earlier last month, we announced the expansion to U.S. military veterans. And now, we’re thrilled to take it one step further and expand this program beyond the U.S. borders, a step that moves us towards bridging the global workforce gap in cybersecurity, and providing new career opportunities for young adults in India.
Cybersecurity threats are a global issue and are on the rise. The number of cyber security incidents reported in 2014 increased globally by 48 per cent to $42.8 million. By 2019 the demand for cyber security professionals is expected to rise to 6 million, but a gap in skills will leave a projected 1.5 million of those positions unfilled.
The partnership between Symantec and NASSCOM comes in response to Indian Prime Minister Narendra Modi’s call at NASSCOM’s silver jubilee on March 1, 2015 to focus on global cybersecurity challenges. In Mike Brown’s address at the launch event, he said, “With the rise in targeted attacks aimed at Indian enterprises and consumers, cybersecurity has become more important than ever before. With the partnership with NASSCOM, we are taking the first big step towards building cyber security skills in India.”
Building Cybersecurity Skills
The initiative will focus on curriculum development for five job roles in line with the National Skills Qualifications Framework, a master training programme. Additionally, there will be scholarships for 1000 women taking NASSCOM cyber security certifications. The programme will also facilitate internships with a goal of employment for certified trainees. Symantec employees will also have opportunities to volunteer as subject matter experts and mentors.
“We’re excited to see the SC3 program expand internationally,” said Cecily Joseph, Vice President Corporate Responsibility. “The cybersecurity skills gap is a global problem, particularly when it comes to reaching women and other underserved populations. The NASSCOM partnership will enable us introduce 1,000 women to careers in cybersecurity, and that’s a great start to addressing this problem in India.”
To learn more about Symantec’s Cyber Career Connection, visit us here.
"How-to" Webcast Series - Ghost Solution Suite 3.0 - July 15th Recording
We held our fourth in our series of "How-to" webcasts for Ghost Solution Suite 3.0 on July 15.
- Download or playback the Webcast here:
- Download the slides from the Webcast
- See attached pdf (scroll to the very bottom of this post)
- Q&A
- full transcript coming soon!
Tweet of the Week

#VtasPart #HPOI with this weeks social digest from @VeritasTechCo at http://bit.ly/1HJcyi3
Veritas Partners (#VtasPart) Harness the Power of Information (#HPOI) with this weeks social digest from our Twitter @veritastechco, LinkedIn& YouTube channels. Simply click share at the top of the page to share this blog post with your professional social networks or follow and share selected stories below.
Veritas Brand
Transforming IT Service Continuity for the Enterprise with Veritas Resiliency Platform (blog)
Twitter: Businesses continue to struggle with #IT continuity. Here’s how @VeritasTechCo has your back: http://symc.ly/1NMlis3 #vtaspart
Linkedin: Predictability, automation and simplicity: three key benefits your organization will gain when adopting the Veritas Technologies Corporations’ Resiliency Platform. Learn more: http://symc.ly/1NMlis3
The world of data is changing – Veritas helps make sense of it all (blog)
Twitter: More than 2/3rds of stored #enterprise data is worthless. Here's how @veritastechco is making it valuable: http://symc.ly/1J6Jly9 #vtaspart
Twitter: #DYK By 2020 there will be more than 44 #zettabytes of data in the world: http://symc.ly/1HsT9Vj @veritastechco #vtaspart
Linkedin: Data continues to collect in waves and many companies drown in excess information. Allow Veritas Technologies Corporation to manage high volumes of data: symc.ly/1J6Jly9
Linkedin: With the ever-increasing amount of data, organizations must focus on their information to complement next-generation infrastructure deployments. Veritas Technologies Corporation’s approach involves three key steps to battle the overflow of data: https://lnkd.in/ezcKTzC
Backup & Recovery
Appliances Spectrum Video (video)
Twitter: Are you getting value out of your data center? Learn about @veritastechco converged #infrastructure: http://symc.ly/1HhUavY #vtaspart
Linkedin: Achieve optimal value and efficiency in your data center with a converged infrastructure. Discover how Veritas Technologies Corporation can help: https://lnkd.in/e9DUMQq
NBU 7.7 Video Teaser (video)
Twitter: In an #IT world of order vs. chaos, where does your #data stand? Let @veritastechco add structure: http://symc.ly/1HxNznL #vtaspart
Linkedin: Mounting data can lead to very large problems for companies who rely on the importance of their information. Enlist in the backup leader to bring structure to unorganized data: http://symc.ly/1HxNznL
Information Availability
Software-Defined Architecture landing page (link)
Twitter: Concentrate on what’s important, lower costs and make decisions on #infostorage with @veritastechco: http://symc.ly/1Hi3zUs #vtaspart
Linkedin: Veritas Technologies Corporation exists to empower you with solutions to help lower costs, mitigate risks and make decisions on information storage: https://lnkd.in/e2cMWjQ
InfoScale: Continuing the Legacy of Application Availability and Storage Management Innovation (blog)
Twitter: Do more with info: meet business #continuity & #data storage needs with @veritastechco's InfoScale. Details: http://symc.ly/1goVoQE #vtaspart
Linkedin: As an integrated portfolio of solutions, Veritas Technologies Corporation’s InfoScale will provide enterprises with agility, heightened performance and efficiency. Learn more: http://symc.ly/1goVoQE
Veritas Information Map Data Sheet (link)
Twitter: Unlock visibility in data by using InfoMap. Here’s how @Veritastech can help you with #infogov decisions. http://symc.ly/1ULj15M #vtaspart
Linkedin: Navigate your data visually with Veritas Technologies Corporation’s InfoMap. See the key features here: : http://symc.ly/1ULj15M
Information Governance
Gartner Market Guide for File Analysis Software (link)
Twitter: #UnstructuredData on your mind? This @Gartner_inc report will help evaluate unanswered questions via @veritastechco: http://symc.ly/1goV4RV #vtaspart
Linkedin: Unstructured data on your mind? The Gartner Market Guide on File Analysis Software will evaluate some of those unanswered questions surrounding information governance and highlight how Veritas Technologies Corporation can help: https://lnkd.in/ecp8MCh
Veritas Debuts Information Map to Visualize your Data Beautifully (blog)
Twitter: Need a road map to untangle the web of #data? @veritastechco is here to help businesses gain info insights: http://symc.ly/1J6Jsd2 #vtaspart
Linkedin: Visualize your company’s data in a whole new light with Veritas Technologies Corporation’s Information Map: https://lnkd.in/esma_jc
Infogov eBook (link)
Twitter: With more than 40% growth, #information explosion is an understatement. Control your data w/ @veritastechco: http://symc.ly/1K4nUk9 #vtaspart
Linkedin: Information explosion is now an understatement and organizations must employ powerful solutions to fight the ever-increasing data curve. Here’s how Veritas Technologies Corporation can help: https://lnkd.in/eymbYmD
Partners, we look forward to helping you innovate, experiment & accelerate in the Veritas Expert Community http://bit.ly/1HJcyi3
Symantec to drive innovation by funding start-ups to take on cyber attackers
Symantec is embracing an open innovation model to deliver advanced cyber security solutions; we are partnering with Frost Data Capital (FDC) to incubate new startup companies to solve hard problems in Internet of Things (IoT) security and cyber security analytics.
As the threat landscape continues to darken and IoT introduces billions of new connected devices, innovative new security approaches are required; the need to innovate and innovate quickly has never been more important. Symantec is expanding our innovation to come from not only inside the company, but to build ecosystems to innovate with partners and customers using a broader, more open approach. This enables us to move beyond our ‘four walls’, encouraging the development of more niche, vertical, and exploratory applications and technologies – that will together deliver the kinds of applications, functionality and features needed in today’s complex world.
Our incubation model is very different than a traditional corporate venture approach where an enterprise invests along side venture capital firms to fund start-ups. We begin by working with our customers and partners to understand the most challenging security issues that they are facing; as we identify the biggest and best ideas, we start companies from the ground up to create solutions to these problems. Symantec and Frost Data Capital will create and seed early-stage start-ups with funding, resources and expertise. These companies will receive access to Symantec’s research telemetry and Frost Data Capital’s data analytics technologies, enabling them to confront the next generation of threats. We believe that analytics will be at the very heart of addressing and resolving many security problems in the future, making it a key part of this new strategy.
Of course, incubation is part of Symantec’s overall innovation model that encompasses R&D innovation, partner innovation, strategic investment, and M&A. Symantec is focused on driving internal R&D innovation: we have increased our internal investment; we have moved to a lean / agile development methodology, and we are delivering platforms that enable our partners and customers to innovate with Symantec in a more seamless way.
The initial plan is to incubate up to 10 companies per year that will deliver advanced cyber security solutions. The Frost Data Capital model to incubate startups works by bringing together seasoned entrepreneurs, a proven innovation methodology and process, and deep expertise in big data analytics, IoT, industrials and healthcare. By partnering with Frost Data Capital, Symantec will be looking to build a solid portfolio of businesses, initially in the US, but then extending our reach into Europe and beyond. We see this as a huge global opportunity for Symantec, its partners and our customers, to drive innovation by leveraging the best ideas and talent to create exciting new security companies.
















